-
United Kingdom+44 (20) 4577-20-00
-
USA+1 (929) 431-18-18
-
Israel+972 (55) 507-70-81
-
Brazil+55 (61) 3772-18-88
-
Canada+1 (416) 850-13-33
-
Czech Republic+420 (736) 353-668
-
Estonia+372 (53) 683-380
-
Greece+30 (800) 000-02-04
-
Ireland+353 (1) 699-43-88
-
Iceland+354 (53) 952-99
-
Lithuania+370 (700) 660-08
-
Netherlands+31 (970) 1027-77-87
-
Portugal+351 (800) 180-09-04
-
Romania+40 (376) 300-641
-
Sweden+46 (79) 008-11-99
-
Slovakia+421 (2) 333-004-23
-
Switzerland+41 (22) 508-77-76
-
Moldova+373 (699) 33-1-22
 English
English
Searching for vulnerabilities on the website
- Main
- Knowledge base
- Searching for vulnerabilities on the website
Site testing allows you to find vulnerabilities and bugs that can be exploited by attackers. If you are a site administrator, we recommend adding penetration testing to your list of tools and regularly searching for vulnerabilities to ensure your sites are fully secure. The issues discovered will help you to fix weaknesses.
Security testing involves so many different tools and tasks. In this article, let's cover the basic aspects of finding vulnerabilities in a website. With the help of these instructions, you will be able to keep your resource safe.
FINDING VULNERABILITIES ON A WEBSITE
Penetration testing and searching for vulnerabilities on a website involves several actions. It's not enough to run one tool and test the site, you need the right approach to help you gather as much information as possible about the security of your system.
The main steps are:
- reconnaissance - searching and gathering information about your network or servers;
- scanning - this step involves checking the site for vulnerabilities based on the information gathered;
- exploitation - this step is optional and not always needed by penetration testers. It is necessary if you need to show the real danger of vulnerabilities;
- patching - at this stage you need to fix all the vulnerabilities found on your site.
Next, let's look at what should be done at each of the stages and what tools you should use for this. It is better not to install all these programs separately, but to use a ready-made environment for penetration testing - Kali Linux. This is a specially prepared Linux distribution that already contains all the necessary programs. This way you don't have to install anything. You can run the system from a flash drive or you can install Kali Linux on your hard disk.
Intelligence
To find out what information other people can learn about your system, you need to apply several tools:
nmap is one of the most popular network scanning tools. You can use it to see what services are running on a website server, what ports they are using, their port versions, and even the operating system version. To see the open ports on your machine run this command in the Kali Linux terminal:
$ nmap -sS 192.168.91.249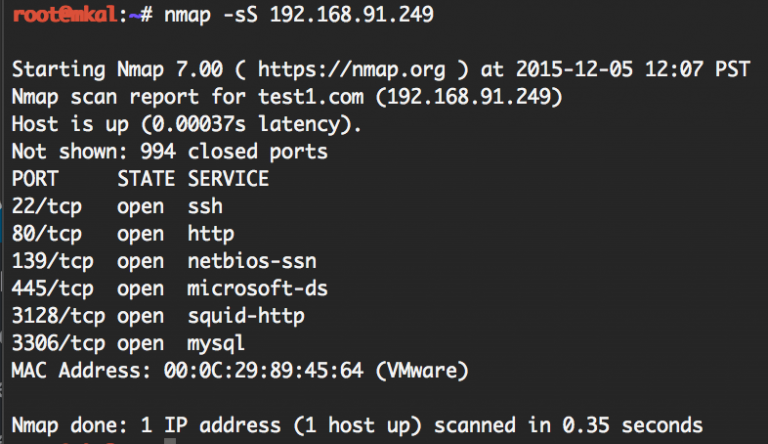
192.168.91.249 is the ip address of the resource. This command displays open ports and service names. You can get more detailed information, for example, you can gather a lot of information about the system already at this point. For example, here you can see that the machine is running an SSH server, a web server, Samba file sharing services, and a proxy server on port 3128. All of these could potentially be vulnerable.
The Nmap scanner allows you to dig deeper, with more intensive scanning. To do this, use the -A option:
$ nmap -A 192.168.91.62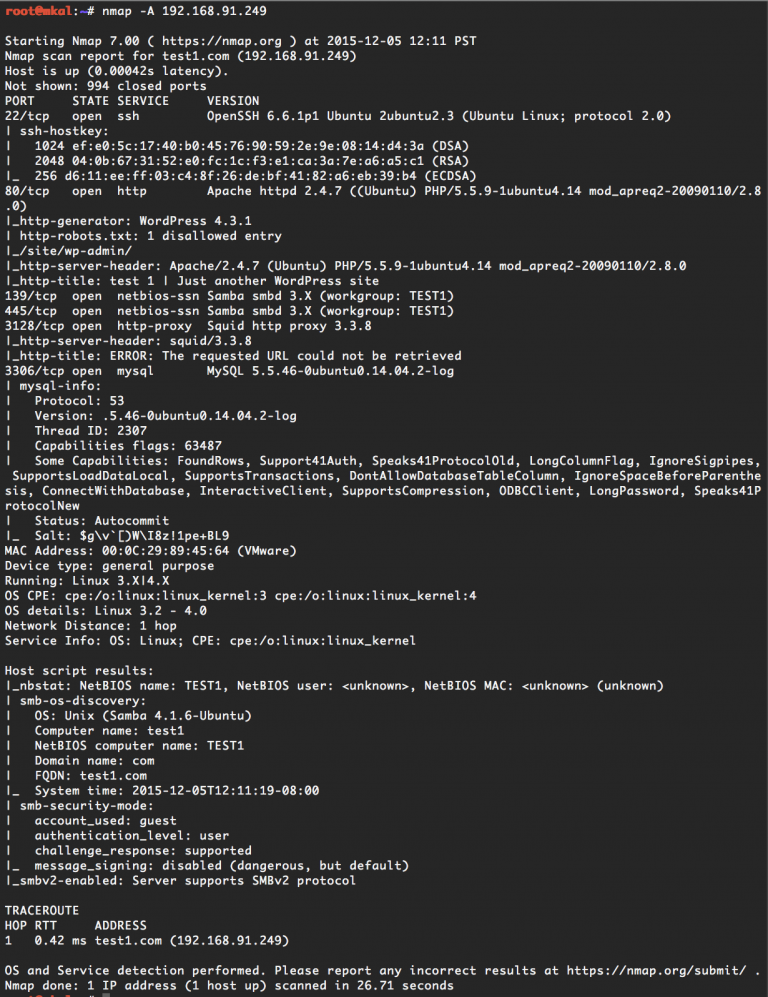
Here you will already see a lot more information, such as service versions, system time, content management system and even the operating system version. Also, if simple vulnerabilities such as a weak FTP password are found, you will know about that too. You can read more about how to use Nmap in a separate article. You should also utilize other available sources of information. It's important to understand what information about you is available online and whether an attacker can get information they shouldn't have access to.
Here are some services:
- whois - you can use this service to find out publicly available information about the domain, registrar, owner, and other contact information;
- recon-ng - a useful analysis tool that comes with Kali Linux;
- Maltego Chlorine is a very popular open source tool for gathering information from open sources;
- Netcraft - a useful tool that allows you to find subdomains of a website;
- hackertarget.com/reverse-ip-lookup - allows you to find out what other sites are running on your ip address.
- Once you have completed the information gathering in the reconnaissance phase, you need to move on to scanning, directly search for vulnerabilities on the Kali Linux site.
Scanning
Fuzzing is often used for scanning. The essence of phasing is to send a large amount of random data to your site to try and find vulnerabilities. The various tools that we will look at below will simulate attacks to test the vulnerability of an application.
Fuzzing applications can identify vulnerabilities, but for the best results it is worth understanding how these applications work and what the bug is. If you have access to the source code of the project, you can use fuzzing and manual analysis in parallel to find problems with greater accuracy. Fuzzing attacks are very loud because they require the transmission of a lot of data. Intrusion protection systems will notice them, you should be careful. Next, let's look at the tools that can be used.
WPScan is an open source project written in Ruby specifically for scanning WordPress. It is very easy to use and can be useful for sites that use a lot of plugins or are not updated. The utility doesn't need source code and performs scans remotely.
Nikto is a vulnerability scanner for websites. It runs much longer than WPSan, but is designed for more than just WordPress. It includes a lot of plugins, and it will run a lot of queries during the scan. For example, the program can find a file that will output phpinfo information. But Nikto generates a lot of false positives, so you need to analyze the output carefully.
Burp Suite is a very powerful program to find vulnerabilities in a website or web applications. This tool works only through a web browser. The utility allows you to check all the forms that are on the website, check the submission of different headers, view browser responses and requests, perform active URL scanning, perform static javascript code analysis, and search for XSS vulnerabilities on the website. It's a great tool, but it can seem complicated.
SQLMap is a program to find sql vulnerabilities of a website. You can find all possible places where SQL injections can be performed. For example, if you assume that there might be a sql injection in the id parameter, use this command
$ sqlmap -u http://example.com/?id=1 -p idThe program will perform testing for different types of databases, so you can specify only the right one:
$ sqlmap --dbms=MySQL -u http://example.com/?id=1 -p idThese commands allow you to test fields, specify different parameters such as databases, tables or passwords.
Exploit
Exploitation completes the search for vulnerabilities on the site and provides the exploitation of vulnerabilities to gain access to the system or data. In general, if you were able to find holes in your security and close them, you don't need to do anything else. But sometimes you need to prove that the problem is really serious.
It is recommended that you do not use vulnerability exploitation on production systems. because it can lead to problems. It is better to create a virtual machine and already in it show everything you need. Here are some tools you can use:
- SQLMap - a tool to find sql vulnerabilities and exploit them;
- Burp Suite - to find XSS vulnerabilities and exploit them;
- Metasploit - exploitation of vulnerabilities in the system.
Metasploit is an entire penetration testing environment that contains many ready-made exploits. You can find exploits for installed plugins or services discovered in the first step. We will take a closer look at how to use Metasploit in a future article.
Patching
This is the final stage of the vulnerability search. Based on everything that was found you need to draw conclusions and close all the holes. When you have all the data about the vulnerabilities. Prioritize and fix everything you found. If you were able to find these vulnerabilities, then anyone else can find them.
Conclusions
In this article, we've done a very crash course in finding website vulnerabilities and reviewed the main website vulnerability finding software that you can use to maximize the security of your resource or infrastructure. Many of these tools are industry standard. Now you can think about your testing strategy and try to eliminate all vulnerabilities.