Partners
Methods of payment
Contact
-
United Kingdom+44 (20) 4577-20-00
-
USA+1 (929) 431-18-18
-
Israel+972 (55) 507-70-81
-
Brazil+55 (61) 3772-18-88
-
Canada+1 (416) 850-13-33
-
Czech Republic+420 (736) 353-668
-
Estonia+372 (53) 683-380
-
Greece+30 (800) 000-02-04
-
Ireland+353 (1) 699-43-88
-
Iceland+354 (53) 952-99
-
Lithuania+370 (700) 660-08
-
Netherlands+31 (970) 1027-77-87
-
Portugal+351 (800) 180-09-04
-
Romania+40 (376) 300-641
-
Sweden+46 (79) 008-11-99
-
Slovakia+421 (2) 333-004-23
-
Switzerland+41 (22) 508-77-76
-
Moldova+373 (699) 33-1-22
 English
English
Site protection: what is it
- Main
- Knowledge base
- Site protection: what is it
11.04.2025, 00:26
Why do you need "Site protection"?
- A website doesn't go down from an attack. Even if thousands of requests are sent to it, the traffic cleaning server will take the hit.
- The real IP of your server remains hidden. This protects against direct attacks.
- Content opens quickly. Requests are served by the servers closest to the user (this works like a CDN).
- Less load on your server. The proxy server itself distributes the cache and handles part of the requests.
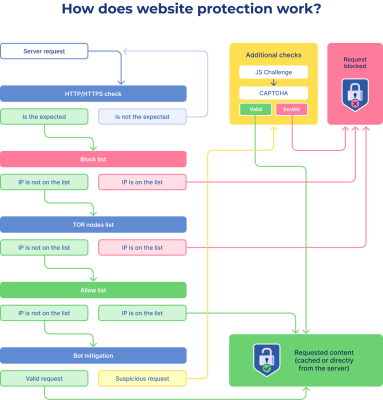
How are requests filtered?
At the application level (L7 OSI), each request goes through a series of filters. Here are the main ones:
- Redirect to HTTPS. All requests redirect to secure connection, if option is enabled.
- Block list. If an IP is on the list, the request is blocked.
- Tor ban. You can block access from Tor networks.
- Allow list. IPs you trust are bypass filters.
- Bot mitigation. The system distinguishes real users from automated scripts.
- Requests are evaluated for attack patterns. Suspicious ones are checked: JS-challenge, CAPTCHA, etc.
 How to order site protection read in the next article.
How to order site protection read in the next article.






































